Identity/Watchdog/Visual Hashing
Visual Hashing
Features
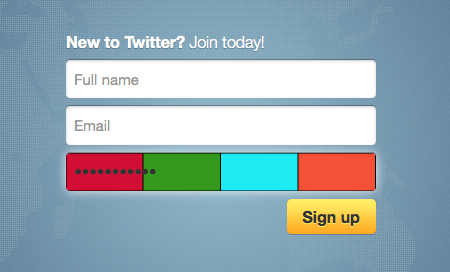
Visual hashing modifies the password input widgets on every page across the web by causing the background of the input to change as the user types to a four color image hash. This hash is calculated from the unsalted SHA1 hash of what has been typed, and is the same (for a given password) across different sites and even browsers. This consistency will help the user realize if they have entered their password correctly without displaying their password on the screen.
The visual hash background disappears after the password widget loses focus.
Screenshot
Implementation
Visual hashing is implemented by including some javascript [1] [2] into every webpage's runtime environment. This script looks for every input in the page's DOM, selects the ones that are password inputs, and then attaches event handlers to onkeydown, onfocus, and onblur.
When the user types inside the input widget (fires onkeydown events), an offscreen <canvas> element is created, on which the visual hash is drawn. The widget's CSS background is set to the canvas' dataURL, until the user types again (in which case the hash is updated) or changes focus from the password input (in which case the widget's original style is restored).
Since the feature can be implemented with just a simple javascript injection, it could be very portable. Currently, it is available as a Jetpack add-on for Firefox, and as a Chrome extension. Porting this functionality to Safari and Internet Explorer should be fairly easy.
Security Concerns
Visual hashing displays an unsalted SHA1 hash of a user's password. This means screenshots will leak information about a user's password, which can then be used for brute force cracking. For this reason, each RGB value in each color of the colorbar is randomly added to a number from -3 to 2. This means each RGB value can take on a total of 6 different states. That means there are a total of (6^3) ^ 4 possible visual hashes per password. This makes it significantly harder to crack a user's password with only a single screenshot. Of course, these differences are unnoticeable to the eye.
The visual hashing feature does not interface with the password manager in any way, and also does not persist any information to disk. The visual hash is only available to the page the input widget is on. Therefore, it should not pose any other security risk.