Security/Reviews/B2G/DownloadManager
Contents
Overview
DRAFT REVIEW: this review is still in progress
FirefoxOS Review Details
- Topic: Downloads WebAPI & Gaia download functionality
- Review Date: January 2014
- Review Leads: Rob Fletcher & Paul Theriault
- Main Bug: https://bugzilla.mozilla.org/show_bug.cgi?id=926955
- Landing: B2G 1.4
Overview
This functionality implements file downloads for Firefox OS. In general, the process is
- A download is initiated by clicking a link in an app or webpage
- Existing code in Gecko (Downloads.jsm) starts downloading the file
- A new Web API, DownloadsAPI.jsm allows web app content to monitor and control downloads
- The Gaia system and settings app use this functionality to present download controls to the user
- The file is downloaded to the sdcard, and opened via web activities (if there is a handler registered for the associated content type
The Download Manager API allows certified web apps (with a permission) to control downloads on Firefox OS. The API allows web apps (as opposed to chrome privileged content on desktop) control downloads by interacting with Downloads.jsm
Key Notes:
- Downloads are initiated in a similar fashion to desktop Firefox (e.g. a HTTP response with content-type of "application/octet-stream" or file-disposition of "attachment;...")
- The files are saved to /sdcard/downloads/ on the filesystem.
- Downloads are opened via web activities. Since the opener application may not have the deviceStorage permission to read the downloaded file, the system/settings app reads the file data into a blob, and passes this as data in the web activity
Scope
The following system components were reviewed:
- Gaia (modified apps)
- System app
- Settings app
- Gecko
- navigator.mozDownloadManager
- interaction with existing Downloads.jsm code
- Gonk
- Interaction with filesystem
Components
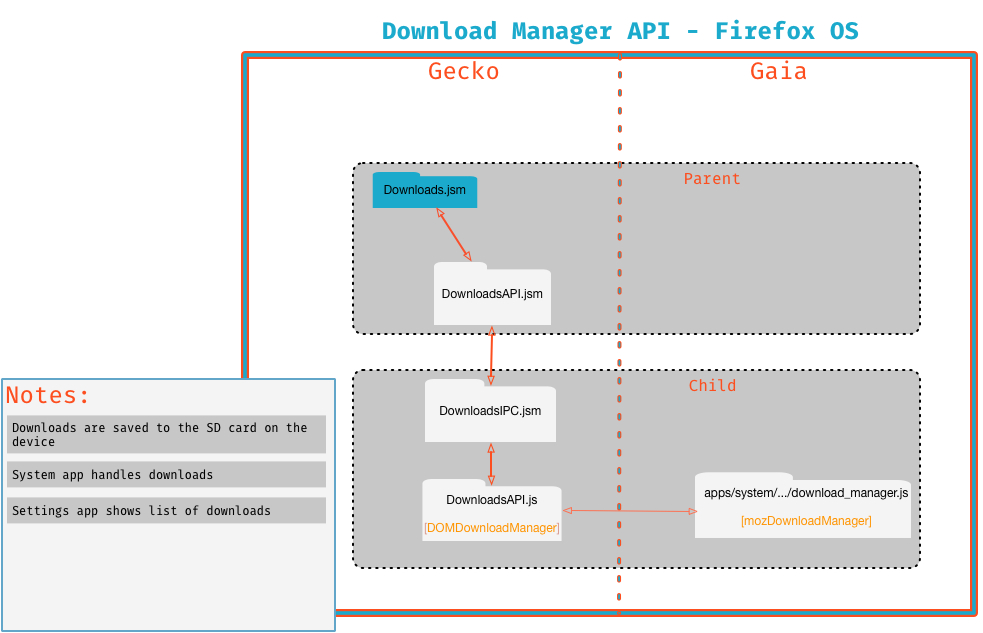
The main components involved in this functionality are:
- Gaia System App: Creates notifications when
DownloadEvents are created (mozDownloadManager.ondownloadstart). Progress is updated as download continues/finishes. Tapping the notification 'opens' the download, which is implemented via firing an appropriate web activity. - Gaia Settings App: uses the mozDownloadManager API to display a list of downloads. User can also launch or delete the download from this list.
- New mozDownloadManager API: provides a mechanism to manage downloads from content (as opposed to chrome)
- Existing Downloads API (Downloads.jsm) manages the initiation and database of downloads (see Downloads.jsm for details)
Relevant Source Code
Gaia
System App
- https://github.com/mozilla-b2g/gaia/blob/master/apps/system/js/download/download_manager.js
- https://github.com/mozilla-b2g/gaia/blob/master/apps/system/js/download/download_notification.js
Settings App
- https://github.com/mozilla-b2g/gaia/blob/master/apps/settings/js/downloads/download_api_manager.js
- https://github.com/mozilla-b2g/gaia/blob/master/apps/settings/js/downloads/download_item.js
- https://github.com/mozilla-b2g/gaia/blob/master/apps/settings/js/downloads/downloads_list.js
- https://github.com/mozilla-b2g/gaia/blob/master/apps/settings/js/downloads/desktop/desktop_moz_downloads.js
- [https://github.com/mozilla-b2g/gaia/blob/master/shared/js/download/download_formatter.js
- [https://github.com/mozilla-b2g/gaia/blob/master/shared/js/download/download_helper.js
- [https://github.com/mozilla-b2g/gaia/blob/master/shared/js/download/download_store.js
- [https://github.com/mozilla-b2g/gaia/blob/master/shared/js/download/download_ui.js
Gecko
WebIDL File for mozDownloadManager
Parent Process
Child Process
- http://mxr.mozilla.org/mozilla-central/source/dom/downloads/src/DownloadsAPI.js
- http://mxr.mozilla.org/mozilla-central/source/dom/downloads/src/DownloadsIPC.jsm
Permission Model
Settings and System are only apps with certified ‘downloads’ permission.
"downloads": {
app: DENY_ACTION,
privileged: DENY_ACTION,
certified: ALLOW_ACTION
},
Review Notes
Gaia
XSS & HTML Injection Attacks
User controlled values are pretty much limited to filename. The filename is displayed in the notifications pull-down as well as the Settings Downloads list. 960749 prevented us from being able to completely check for HTML injections. (See Future Work below)
Based on source code inspection, there are no dangerous coding practices (like misuse of innerHTML) that will result in HTML/JS injections.
Characters ',",>, \, & and < were tested in filenames. We could not directly test > or < because the filesystem disallowed those characters in filenames, however we did use App Manager to break into the JS and insert those characters to see if filenames were rendered safely in the Notifications pull down as well as the Settings->Downloads menu.
Secure Communications
Not relevant.
Secure Data Storage
Downloads are stored on the SDcard, which is appropriate for user content.
Denial of Service
See 960739
Interfaces with other Apps/Content
gaia/apps/system/js/download/download_notification.js
Used to launch Settings->Download list
183 var activity = new MozActivity({
184 name: 'configure',
185 data: {
186 target: 'device',
187 section: 'downloads'
188 }
189 });
Used to open file after download
176 var activity = new MozActivity({
177 name: 'open',
178 data: {
179 url: download.path,
180 type: contentType,
181 blob: blob
182 }
Gecko
1. Content/Chrome Segregation
DownloadsAPI is implemented using WebIDL. There was a lot of discussion around what to expose in the case when a page does not have the permission present - see bug 957592 for details.
2. Process Segregation
Inter-process communication is performed through DownloadsIPC.jsm & DownloadsAPI.jsm. We are mainly interested in the message which the parent listens for:
- Downloads:GetList
- Downloads:ClearAllDone
- Downloads:Remove
- Downloads:Pause
- Downloads:Resume
Permissions are checked in the parent before processing any messages, using the standard approach:
144 receiveMessage: function(aMessage) {
145 if (!aMessage.target.assertPermission("downloads")) {
146 debug("No 'downloads' permission!");
147 return;
148 }
One issue was identified in the way the message was processed however - see bug 966141 for details.
3. Data validation & Sanitization
The API accepts only minimal data from content, and as such the attack surface is very small, and no issues were found.
4. Denial of Service
960739 was identified as a potential DoS scenario.
Security Risks & Mitigating Controls
- Unsanitized filename/content leads to injection issues
- Some testing already ready
- Code review of Gaia system app reveals usage of existing NotificationScreen object, which uses .textContent, so is safe from XSS
- Likewise, settings app creates HTML safely. see download_item.js
- Exhausting of disk space
- Files are stored in /sdcard/downloads, which mitigates the impact to a user.
- Providing secure access to opener applications
- Files are stored on the SDcard, when a download is opened, system app/settings app gets the file contents with deviceStorage API, then puts the content in a blob, which is sent via a web activity to the opener application
- Needs more investigation: is there any way to attack opener application, or coerce system/settings to open the wrong file?
Actions & Recommendations
- bug 948029
- bug 966141