Security/Sandbox
Contents
Overview
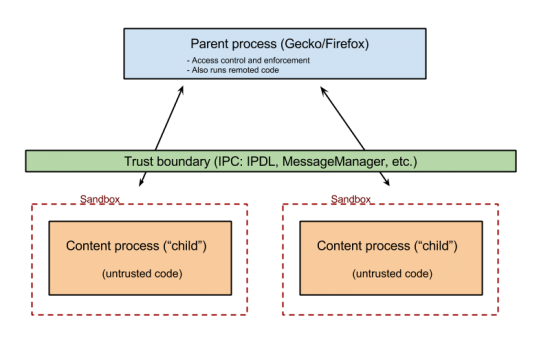
Security Sandboxing makes use of child processes as a security boundary. The process model, i.e. how Firefox is split into various processes and how these processes interact between each other is common to all platforms. For more information see the Electrolysis wiki page, and its sucessor, Project Fission. The security aspects of a sandboxed child process are implemented on a per-platform basis. See the Platform Specifics section below for more information.
Technical Docs
Current Status
| Sandbox | Trunk | Beta | Release | |||
|---|---|---|---|---|---|---|
| Level | Level | Version | Level | Version | ||
| Windows (content) | Level 6 | Level 6 | Fx76 | Level 6 | Fx76 | |
| Windows (compositor) | Level 1 | Level 1 | Level 1 | |||
| Windows (GMP) | enabled | enabled | enabled | |||
| Windows (Socket) | Level 1 | Level 1 | Fx75 | Level 1 | Fx75 | |
| OSX (content) | Level 3 | Level 3 | Fx56 | Level 3 | Fx56 | |
| OSX (GMP) | enabled | enabled | enabled | |||
| OSX (RDD) | enabled | enabled | enabled | |||
| OSX (Socket) | enabled | disabled | disabled | |||
| Linux (content) | Level 4 | Level 4 | Fx60 | Level 4 | Fx60 | |
| Linux (GMP) | enabled | enabled | enabled | |||
A 'level' value reflects unique sandbox security settings for each platform and process. Most processes only have two "active" levels, the current setting and a lower (previous released) setting. Level settings other than these two values carry no guarantee of altering security behavior, level settings are primarily a release rollout debugging feature.
Windows
Content
Sandbox security related setting are grouped together and associated with a security level. Lower level values indicate a less restrictive sandbox.
| Sandbox Feature | Level 6 | Level 7 (Release) | Level 8 (Nightly) |
|---|---|---|---|
| Job Level | JOB_LOCKDOWN | JOB_LOCKDOWN | JOB_LOCKDOWN |
| Access Token Level | USER_LIMITED | USER_LIMITED | USER_RESTRICTED |
| Alternate Desktop | YES | YES | YES |
| Alternate Windows Station | YES | YES | YES |
| Initial Integrity Level | INTEGRITY_LEVEL_LOW | INTEGRITY_LEVEL_LOW | INTEGRITY_LEVEL_LOW |
| Delayed Integrity Level | INTEGRITY_LEVEL_LOW | INTEGRITY_LEVEL_UNTRUSTED | INTEGRITY_LEVEL_UNTRUSTED |
| Mitigations |
MITIGATION_BOTTOM_UP_ASLR |
MITIGATION_BOTTOM_UP_ASLR |
MITIGATION_BOTTOM_UP_ASLR |
| Delayed Mitigations |
MITIGATION_STRICT_HANDLE_CHECKS |
MITIGATION_STRICT_HANDLE_CHECKS |
MITIGATION_STRICT_HANDLE_CHECKS |
Gecko Media Plugin (GMP)
| Sandbox Feature | Level |
|---|---|
| Job Level | JOB_LOCKDOWN |
| Access Token Level | USER_LOCKDOWN, USER_RESTRICTED[1] |
| Initial Integrity Level | INTEGRITY_LEVEL_LOW |
| Delayed Integrity Level | INTEGRITY_LEVEL_UNTRUSTED |
| Alternate desktop | yes |
| Mitigations |
MITIGATION_BOTTOM_UP_ASLR |
| Delayed Mitigations |
MITIGATION_STRICT_HANDLE_CHECKS |
[1] depends on the media plugin
Remote Data Decoder (RDD)
| Sandbox Feature | Level |
|---|---|
| Job Level | JOB_LOCKDOWN |
| Access Token Level | USER_LIMITED |
| Initial Integrity Level | INTEGRITY_LEVEL_LOW |
| Delayed Integrity Level | INTEGRITY_LEVEL_LOW |
| Alternate desktop | yes |
| Mitigations |
MITIGATION_BOTTOM_UP_ASLR |
| Delayed Mitigations |
MITIGATION_STRICT_HANDLE_CHECKS |
OSX
Content Levels for Web and File Content Processes
Mac content processes use sandbox level 3. File content processes (for file:/// origins) also use level 3 with additional rules to allow read access to the filesystem. Levels 1 and 2 can still be enabled in about:config, but they are not supported and using them is not recommended. Different sandbox levels were used for testing and debugging during rollout of Mac sandboxing features, but they now are planned to be removed. Mac sandboxing uses a white list policy for all process types. Each policy begins with a statement to deny all access to system resources and then specifies the allowed resources. The level 3 sandbox allows file system read metadata access with full read access for specific system directories and some user directories, access to the microphone, access to various system services, windowserver, named sysctls and iokit properties, and other miscellaneous items. Work is ongoing to remove access to the microphone, windowserver, and other system services where possible. The sandbox blocks write access to all of the file system, read access to the profile directory (apart from the chrome and extensions subdirectories, read access to the home directory, inbound/outbound network I/O, exec, fork, printing, video input devices such as cameras. Older sandbox levels 1 and 2 are less restrictive. Mainly, level 2 allows file-read access to all of the filesystem except the ~/Library directory. Level 1 allows all file-read access. Level 1 restrictions are a subset of level 2. Level 2 restrictions are a subset of level 3.
The web and file content policy is defined in SandboxPolicyContent.h
Gecko Media Plugin Processes
The Gecko Media Plugins (GMP) policy is defined in SandboxPolicyGMP.h.
Remote Data Decoder Processes
The Remote Data Decoder (RDD) policy is defined in SandboxPolicyUtility.h.
Socket Process
The socket process policy is defined in SandboxPolicySocket.h. At this time (May 2020), the socket process sandbox is only used on the Nightly channel and only for WebRTC networking.
Linux
Content Levels
| Job Level | What's Blocked by the Sandbox? |
|---|---|
| Level 1 |
|
| Level 2 |
|
| Level 3 |
|
| Level 4 |
|
Content Rules
Gecko Media Plugin
Customization Settings
The Linux sandbox allows some amount of control over the sandbox policy through various about:config settings. These are meant to allow more non-standard configurations and exotic distributions to stay working - without compiling custom versions of Firefox - even if they can't be directly supported by the default configuration.
See Activity Logging for information on how to debug these scenarios.
security.sandbox.content.level
- See Content Levels above. Reducing this can help identify sandboxing as the cause of a problem, but you're better of trying the more fine grained permissions below.
security.sandbox.content.read_path_whitelist
security.sandbox.content.write_path_whitelist
- Comma-separated list of additional paths that the content process is allowed to read from or write to, respectively. To allow access to an entire directory tree (rather than just the directory itself), include a trailing / character.
security.sandbox.content.syscall_whitelist
- Comma-seperated list of additional system call numbers that should be allowed in the content process. These affect the seccomp-bpf filter.
Preferences
| Process Type | Preference Type | Preference |
|---|---|---|
| Content | numerical | security.sandbox.content.level |
| Windows NPAPI Plugin | numerical | dom.ipc.plugins.sandbox-level.default dom.ipc.plugins.sandbox-level.<plugintype> |
| Compositor | numerical | security.sandbox.gpu.level |
| Media | Embedded | N/A |
Note - Levels greater than the current default for a particular process type are not implemented.
File System Restrictions
Sandboxing enforces file system write and read restrictions for XUL based add-on content (frame and process) scripts. To avoid issues as sandboxing features roll out add-on authors should update their legacy add-on code today such that content scripts no longer attempt to read or write from restricted locations. Note these restrictions do not affect WebExtension content script or XUL add-on script running in the browser process.
File system access rules for content processes, reverse precedence:
| Location | Access Type | Restriction |
|---|---|---|
| file system | read/write | deny by default |
| install location | write | deny |
| install location | read | allow |
| system library locations | write | deny |
| system library locations | read | allow |
| profile/* | read/write | deny by default |
| profile/extensions | write | deny |
| profile/extensions | read | allow |
Debugging Features
Activity Logging
The following prefs control sandbox logging. On Windows, output is sent to the Browser Console when available, and to a developer console attached to the running browser process. On OSX, once enabled, violation log entries are visible in the Console.app (/Applications/Utilities/Console.app). On Linux, once enabled, violation log entries are logged on the command line console.
security.sandbox.logging.enabled (boolean)
security.sandbox.windows.log.stackTraceDepth (integer, Windows specific)
The following environment variables also triggers sandbox logging output:
MOZ_SANDBOX_LOGGING=1
OSX Specific Sandbox Logging
On Mac, sandbox violation logging is disabled by default. To enable logging,
- Launch the OS X Console app (/Applications/Utilities/Console.app) and filter on "plugin-container".
- Either set the pref security.sandbox.logging.enabled=true and restart the browser OR launch the browser with the MOZ_SANDBOX_LOGGING environment variable set.
Linux specific Sandbox Logging
The following environment variable triggers extra sandbox debugging output:
MOZ_SANDBOX_LOGGING=1
Environment variables
| ENVIRONMENT VARIABLE | DESCRIPTION | PLATFORM |
|---|---|---|
| MOZ_DISABLE_CONTENT_SANDBOX | Disables content process sandboxing for debugging purposes. | All |
| MOZ_DISABLE_GMP_SANDBOX | Disable media plugin sandbox for debugging purposes | All |
| MOZ_DISABLE_NPAPI_SANDBOX | Disable 64-bit NPAPI process sandbox | Windows and Mac |
| MOZ_DISABLE_GPU_SANDBOX | Disable GPU process sandbox | Windows |
| MOZ_DISABLE_RDD_SANDBOX | Disable Data Decoder process sandbox | All |
| MOZ_DISABLE_SOCKET_PROCESS_SANDBOX | Disable Socket Process process sandbox | All |
Setting a custom environment in Windows
1) Close Firefox
2) Browser to the location of your Firefox install using Explorer
3) Shift + Right-click in the folder window where firefox.exe is located, select "Open command window here"
4) Add the environment variable(s) you wish to set to your command window -
set MOZ_DISABLE_NPAPI_SANDBOX=1(return)
5) enter firefox.exe and press enter to launch Firefox with your custom environment
Local Build Options
To disable building the sandbox completely build with this in your mozconfig:
ac_add_options --disable-sandbox
To disable just the content sandbox parts:
ac_add_options --disable-content-sandbox
Bug Lists
Priorities
Security/Process Sandboxing Lists
Triage Lists
- Sandboxing Triage List: https://is.gd/ghRoW8
- Lists sandboxing component bugs that are not tracked by a milestone
- Ignores previously triaged into either sb- or sb+
- Ignores meta bugs and bugs with needinfos
- Global Triage List
- Lists any bug in the database with sb?
- Ignores bugs with needinfos
- sb+ triage list
- Previously triaged bugs that have no milestone and no priority set
- sb? needinfos: http://is.gd/dnSyBs
- webrtc specific sandboxing bugs: https://is.gd/c5bAe6
- sb tracking + 'webrtc'
Roadmap
2020 H1 - Main work focus
- Remote Canvas Drawing operations,
- Prerequisite for win32k.sys lockdown.
- Remote Form widget drawing,
- Prerequisite for win32k.sys lockdown.
- Follow-ups in Bug for defaulting it on
- Remote WebGL drawing,
- See also Out-of-process WebGL compositing.
- Follow-ups in Make it shippable bug.
- Sandbox the GPU Process.
- Stalled on non-reproducible field issues.
- Remote Look and Feel + Theming.
- Prerequisite for win32k.sys lockdown.
- Shared memory with read-only and read/write mode.
- Security and memory usage win.
- Use memfd_create for shared memory.
- Performance win and would solve many issues with people running into problems with the default docker/kubernetes configurations that only give a tiny amount of shared memory.
- Enable further telemetry for third-party process injection.
2020 H2 - Main work focus
- Carry-over of win32k.sys lockdown prerequisites from 2020 H1.
- Carry-over of stalled GPU sandboxing work.
- Remaining win32k.sys blockers.
- Enable CIG in RDD.
- Investigate/experiment with feasibility of shipping CIG in content.
Communication
| Weekly Team Meeting | Thursday at 8:00am PT
|
| Matrix |
|
People
| Engineering Management |
|
| Project Management |
|
| QA |
|
| Development Team |
|
Repo Module Ownership
Links
- Electrolysis Wiki Page (lot of additional resource links)
- Security/Sandbox/macOS_Release - description of what to do when a new macOS release comes out in order to find out what updates they made to the sandbox.
- Chromium Sandbox
- Apple's Sandbox guide
- "Introducing Chrome's next-generation Linux sandbox" (seccomp-bpf related)
- Native Client on Wikipedia (Links to papers on Native Client's design and use of SFI, as well as papers on SFI itself.)
- Features of Protected Mode in Internet Explorer
B2G Archive
B2G has always been “sandboxed” to some extent; every app/tab gets its own content process, which uses the Android security model: a separate uid per process, no group memberships, and kernel patches that require group membership for things like network access. But privilege escalation via kernel vulnerabilities is relatively common, so we also use the seccomp-bpf system call filter to reduce the attack surface that a compromised content process can directly access.